OSI Model: This is a conceptual model which was published in the year 1984 by ISO (International Organization for Standardization) to establish a standard for network design and other related compute/hardware equipments.
OSI stands for Open Systems Interconnection Model. In modern times, OSI model is only used for references.
A glimpse of OSI model reference is shown below:
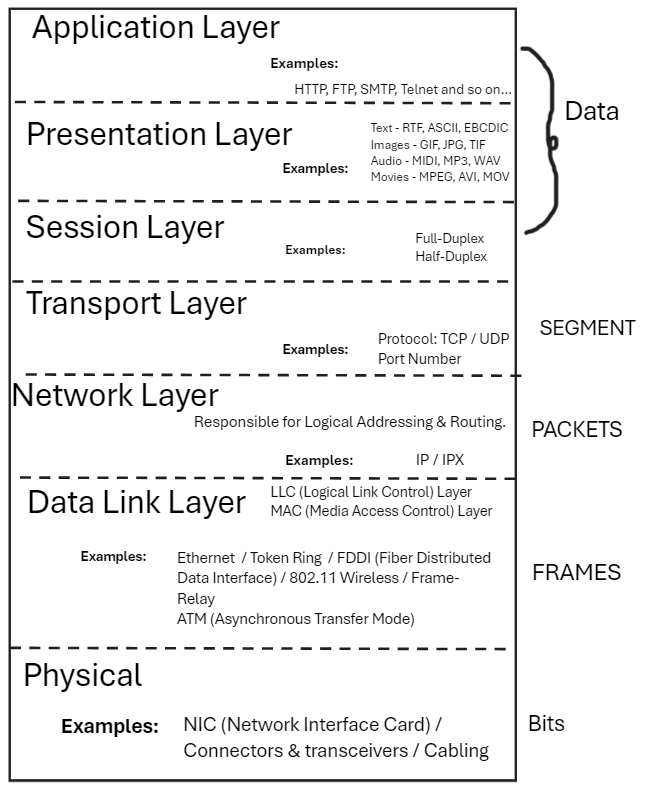
The above representation of OSI Model will help in understanding the technologies that are used in modern times and where each pieces of the respective technologies fits into. The examples shared in most of the layer, well the examples can go beyond the above mentioned ones (the list is long, for example in Application layer) but for demonstration purposes we have given few names for reference purposes.
Conclusion: OSI model resonates to theoritical framework.
TCP/IP Model: The DoD (Department of Defense) developed their own networking model which consists of four layers whereas the OSI model has a seven layer approach.
The TCP/IP model has more practical approach.
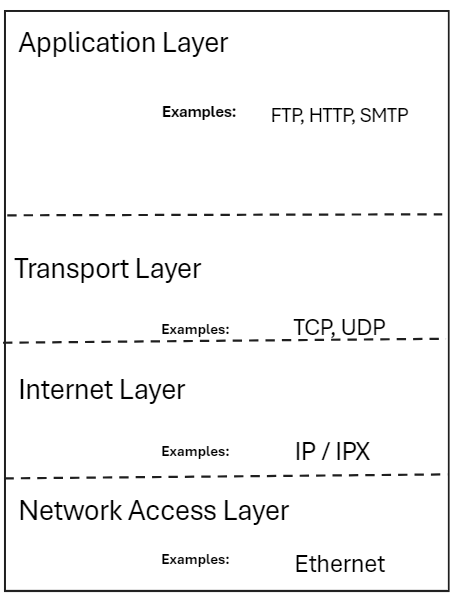
In terms of networking and comparing with the given models, whenever debuging any scenarios TCP/IP model has the closest or the best approach. In terms of understanding each layer in detail then OSI model is the best way to understand each layer. Hence it is said that OSI model is more of a theoritical approach while TCP/IP model has more of a practical approach.
Explanation of each layer with respect to OSI layer (theoritical framework):
The Application layer is the topmost layer of both the OSI and TCP/IP models (Layer 7 in OSI, and Layer 4 in TCP/IP). It is responsible for directly interacting with software applications to provide network services to end users. This layer enables communication between networked applications and manages application-specific protocols.
Here are some examples of Application Layer protocols and services, along with their functions:
1. HTTP (Hypertext Transfer Protocol)
- Description: HTTP is the protocol used by web browsers and web servers to communicate and exchange web pages, allowing users to view and navigate the internet.
- Uses: Web browsing, accessing websites, loading web content (HTML, CSS, images, etc.).
- Examples: Websites, online applications like Google Docs, and APIs.
- Related protocol: HTTPS (Secure HTTP) adds encryption using SSL/TLS for secure communication.
2. FTP (File Transfer Protocol)
- Description: FTP is used for transferring files between computers on a network.
- Uses: Uploading and downloading files from a remote server, commonly used for managing website files.
- Examples: FileZilla (FTP client), remote server management for websites.
- Related protocol: SFTP (Secure File Transfer Protocol) is a secure version of FTP.
3. SMTP (Simple Mail Transfer Protocol)
- Description: SMTP is used for sending emails between mail servers.
- Uses: Email transmission and delivery, typically between email servers and from client to server.
- Examples: Sending emails through services like Gmail, Outlook, and Yahoo.
- Related protocol: IMAP or POP3 are used for receiving emails.
4. DNS (Domain Name System)
- Description: DNS translates human-readable domain names (like www.example.com) into IP addresses that computers use to identify each other on a network.
- Uses: Domain name resolution, allowing users to access websites using domain names instead of IP addresses.
- Examples: Accessing websites like www.google.com; DNS lookup tools.
5. DHCP (Dynamic Host Configuration Protocol)
- Description: DHCP dynamically assigns IP addresses to devices on a network, simplifying the process of configuring IP addresses.
- Uses: Automatic IP address allocation to devices like computers, phones, and printers.
- Examples: Connecting to Wi-Fi, network configuration in homes and offices.
6. Telnet
- Description: Telnet is a protocol used for remote command-line access to another computer over a network.
- Uses: Accessing and managing remote servers.
- Examples: Remote administration of servers and network devices.
- Related protocol: SSH (Secure Shell) is a secure version of Telnet.
7. SNMP (Simple Network Management Protocol)
- Description: SNMP is used to manage and monitor network devices like routers, switches, and servers.
- Uses: Network monitoring, collecting data, and configuring network devices.
- Examples: Network management systems (NMS) like Nagios, SolarWinds.
8. POP3 (Post Office Protocol v3)
- Description: POP3 is used by email clients to retrieve emails from a mail server, usually downloading them locally.
- Uses: Retrieving emails from a server and storing them on a local device.
- Examples: Outlook, Thunderbird, and other email clients.
- Related protocol: IMAP (Internet Message Access Protocol) allows emails to be stored on the server and synchronized across multiple devices.
9. IMAP (Internet Message Access Protocol)
- Description: IMAP is used for accessing and managing emails stored on a server, allowing multiple devices to view synchronized email data.
- Uses: Email management and synchronization across devices.
- Examples: Gmail, Yahoo Mail, Outlook when using email clients.
10. NTP (Network Time Protocol)
- Description: NTP is used to synchronize the clocks of computers over a network to ensure accurate timekeeping.
- Uses: Time synchronization for servers, workstations, and network devices.
- Examples: Synchronizing clocks on computers, routers, and other network devices.
The Presentation Layer (Layer 6) in the OSI model is responsible for data translation, encryption, compression, and formatting. It ensures that data sent from the application layer of one system can be understood by the application layer of another, regardless of differences in data format.
Here are some examples of Presentation Layer protocols and functions:
1. MIME (Multipurpose Internet Mail Extensions)
- Description: MIME is used to encode and format different types of data (like images, audio, and attachments) so that it can be sent via email.
- Function: Converts non-text data (like images or audio files) into a text-based format so it can be easily transmitted over email systems.
- Use Case: Sending email attachments such as pictures, videos, or documents (e.g., Gmail or Outlook).
2. SSL/TLS (Secure Sockets Layer / Transport Layer Security)
- Description: SSL and TLS provide encryption for secure communication over a network.
- Function: Encrypts data at the presentation layer, ensuring privacy and data integrity during transmission.
- Use Case: Secure browsing on websites (HTTPS), secure email communication, and secure file transfers.
3. JPEG (Joint Photographic Experts Group) / GIF (Graphics Interchange Format)
- Description: JPEG and GIF are common image formats used for compressing images.
- Function: These formats compress and translate images for efficient transmission over networks and display on different devices.
- Use Case: Sending and receiving images via web browsers or email services.
4. ASCII (American Standard Code for Information Interchange)
- Description: ASCII is a character encoding standard that represents text in computers.
- Function: Converts characters into a standardized numerical code, ensuring compatibility between different systems.
- Use Case: Text data transmission between computers and devices using different software or platforms.
5. EBCDIC (Extended Binary Coded Decimal Interchange Code)
- Description: EBCDIC is another character encoding scheme used in older IBM mainframes.
- Function: Translates and formats data to ensure compatibility with mainframe systems.
- Use Case: Data communication between legacy IBM systems and modern computers.
6. MP3 (MPEG-1 Audio Layer 3)
- Description: MP3 is a widely used audio compression format.
- Function: Compresses and encodes audio data for efficient transmission and storage.
- Use Case: Streaming or downloading music on services like Spotify or iTunes.
7. MP4 (MPEG-4 Part 14)
- Description: MP4 is a digital multimedia container format used for storing video, audio, and other data.
- Function: Encodes and compresses video and audio data for transmission over the internet or for storage on devices.
- Use Case: Streaming video services like YouTube or Netflix.
8. Data Compression Algorithms (e.g., ZIP, RAR)
- Description: Data compression algorithms reduce the size of files for faster transmission.
- Function: Compresses data to save bandwidth and storage space.
- Use Case: Sending large files over the internet or storing them efficiently (e.g., ZIP files sent as email attachments).
9. XML (Extensible Markup Language) and JSON (JavaScript Object Notation)
- Description: XML and JSON are data formats used for encoding data structures for transmission between systems.
- Function: Ensures that data is structured in a format that is easily readable by different systems.
- Use Case: Web APIs, data exchange between client and server, and configuration files.
10. Unicode
- Description: Unicode is a universal character encoding standard that represents text across different platforms and languages.
- Function: Ensures that text is consistently represented in all systems, regardless of language or platform.
- Use Case: International text communication, including web browsers and applications.
Functions of the Presentation Layer:
- Data translation: Converts data from one format to another to ensure compatibility between different systems.
- Data encryption/decryption: Protects sensitive information by encoding it before transmission and decoding it upon receipt.
- Data compression/decompression: Reduces the size of data to save bandwidth during transmission and storage.
The Session Layer (Layer 5) of the OSI model is responsible for establishing, managing, and terminating communication sessions between two devices. It ensures that sessions are maintained, data streams are synchronized, and communications are properly managed, including handling the start, continuation, and end of conversations.
Here are some examples of Session Layer protocols and concepts:
1. NetBIOS (Network Basic Input/Output System)
- Description: NetBIOS provides services related to the session layer, allowing applications on different computers to communicate over a local area network (LAN).
- Function: Establishes sessions between computers to share resources like files and printers.
- Use Case: File sharing between computers on the same network using Windows.
2. RPC (Remote Procedure Call)
- Description: RPC allows a program to execute a procedure (function) on a remote server as if it were local.
- Function: Manages the session between client and server during the remote execution of tasks.
- Use Case: Used in distributed computing to execute commands across different devices in a network.
3. SIP (Session Initiation Protocol)
- Description: SIP is used to establish, maintain, and terminate multimedia communication sessions such as voice and video calls.
- Function: Manages VoIP sessions, including call setup, control, and termination.
- Use Case: Widely used in voice over IP (VoIP) communication systems like Zoom, Skype, and FaceTime.
4. PPTP (Point-to-Point Tunneling Protocol)
- Description: PPTP is used to establish VPN sessions between remote users and secure networks.
- Function: Manages the session during a VPN connection.
- Use Case: Provides secure communication between remote users and company networks.
5. SQL Session Management
- Description: In databases like SQL, sessions are established between a user and a database server.
- Function: Manages the session for database queries, ensuring that a connection is properly opened and closed.
- Use Case: User-to-database interaction during data retrieval or manipulation.
6. AppleTalk Session Protocol (ASP)
- Description: AppleTalk’s ASP manages communication sessions between network devices on older Macintosh networks.
- Function: Facilitates communication between client and server processes on AppleTalk networks.
- Use Case: Was used in legacy Apple networks for managing resources like printers and file servers.
7. X.225 or ITU-T Recommendation (Session Layer Protocol)
- Description: A protocol that defines the functions and procedures necessary for session layer services.
- Function: Provides services for session establishment, maintenance, and termination.
- Use Case: Used in OSI-based networks for session management and connection control.
8. ISO 8327
- Description: This is the OSI session protocol standard, which provides a framework for managing sessions between computers.
- Function: Supports the establishment and control of sessions between entities in an OSI-based network.
- Use Case: Applied in networks where OSI-compliant standards are necessary.
Session Layer Functions:
- Session establishment: Creates a logical link between two devices for communication.
- Session maintenance: Keeps the connection active, handling errors and ensuring synchronization between devices.
- Session termination: Properly closes the session after data exchange, ensuring a clean end to the connection.
The Transport Layer (Layer 4 of the OSI model and Layer 3 of the TCP/IP model) is responsible for providing end-to-end communication services for applications, including reliable data transfer, flow control, error detection, and multiplexing. It ensures that data is delivered error-free, in sequence, and without losses or duplications.
Here are some examples of Transport Layer protocols and concepts:
1. TCP (Transmission Control Protocol)
- Description: TCP is a connection-oriented protocol that ensures reliable, ordered, and error-checked delivery of data between applications.
- Functions:
- Establishes a connection between sender and receiver before data transfer (handshake).
- Ensures that data is delivered in sequence and without errors.
- Provides flow control and congestion control.
- Use Case: Used in applications like web browsing (HTTP/HTTPS), email (SMTP, IMAP), and file transfers (FTP).
2. UDP (User Datagram Protocol)
- Description: UDP is a connectionless protocol that provides fast, but unreliable, data transfer.
- Functions:
- Does not establish a connection, so it’s faster than TCP.
- No guarantee of delivery, order, or error correction.
- Use Case: Suitable for real-time applications like online gaming, live video streaming, VoIP (Skype, Zoom), and DNS lookups.
3. SCTP (Stream Control Transmission Protocol)
- Description: SCTP is a transport layer protocol that combines features of both TCP and UDP. It supports multiple streams of data within a single connection and is designed for message-oriented communication.
- Functions:
- Provides reliable, ordered delivery of messages.
- Supports multi-homing (a host can be connected to multiple IP addresses).
- Use Case: Used in applications like telecommunication signaling (SS7), VoIP, and transport of web services.
4. DCCP (Datagram Congestion Control Protocol)
- Description: DCCP is a transport layer protocol that provides connection-oriented datagram service with congestion control.
- Functions:
- Provides features like congestion control, but without reliable delivery.
- Optimized for multimedia and streaming applications.
- Use Case: Useful in streaming media and telephony, where maintaining throughput is more important than reliable delivery.
5. SPX (Sequenced Packet Exchange)
- Description: SPX is a connection-oriented protocol used in the older Novell NetWare networking system.
- Functions:
- Provides reliable, sequenced delivery of packets.
- Similar to TCP in that it guarantees delivery and ensures proper sequence of data.
- Use Case: Was used in legacy Novell networks, but has mostly been replaced by TCP/IP.
6. TLS (Transport Layer Security) / SSL (Secure Sockets Layer)
- Description: While primarily used in the Application layer, TLS/SSL also operates at the Transport Layer by securing the communication between devices through encryption.
- Functions:
- Ensures secure transmission of data between client and server by encrypting the data.
- Use Case: HTTPS web traffic, secure email (SMTPS), and VPNs. Also refer: https://learn.microsoft.com/en-us/windows-server/security/tls/transport-layer-security-protocol & rfc: https://datatracker.ietf.org/doc/html/rfc5246
7. Flow Control (e.g., Sliding Window Protocol)
- Description: Flow control mechanisms at the Transport Layer manage the pace of data transmission to ensure that the sender does not overwhelm the receiver with too much data at once.
- Functions:
- Adjusts the data rate to prevent network congestion and loss of data.
- Use Case: Used in TCP’s sliding window protocol to regulate traffic.
8. Error Detection and Correction (e.g., Checksums)
- Description: Transport Layer protocols like TCP use checksums to detect errors in transmitted data.
- Functions:
- Ensures that data is transmitted without corruption by checking for errors and retransmitting if needed.
- Use Case: Used in TCP for error detection and correction during data transmission.
Summary of Functions of the Transport Layer:
- Connection establishment/termination: TCP establishes and terminates connections through a three-way handshake.
- Reliability: TCP ensures reliable delivery of data using error detection, correction, and retransmission.
- Flow control: Manages the rate of data flow to avoid overwhelming the receiver.
- Multiplexing: Multiple applications can share the same network connection, identified by port numbers.
- Error detection: Ensures data integrity using checksums.
The Transport Layer plays a critical role in ensuring that data is reliably transmitted between devices, especially in protocols like TCP, while protocols like UDP focus on speed and efficiency for real-time applications.
The Network Layer (Layer 3 in the OSI model and the Internet Layer in the TCP/IP model) is responsible for routing, logical addressing (IP addresses), and forwarding data packets across different networks. It ensures that data is sent from the source device to the destination device, even if the devices are in different networks.
Here are some examples of Network Layer protocols and concepts:
1. IP (Internet Protocol)
- Description: IP is the primary protocol for routing data across networks. It provides logical addressing and packet forwarding.
- Functions:
- Assigns logical IP addresses to devices.
- Routes packets of data from the source to the destination across different networks.
- Types:
- IPv4: Uses 32-bit addresses, most commonly used.
- IPv6: Uses 128-bit addresses, designed to replace IPv4 due to address exhaustion.
- Use Case: Data transmission over the internet (e.g., browsing the web, video streaming).
2. ICMP (Internet Control Message Protocol)
- Description: ICMP is used by network devices, like routers, to send error messages and operational information.
- Functions:
- Provides feedback on network issues (e.g., unreachable destinations, packet loss).
- Used for diagnostic tools like ping and traceroute.
- Use Case: Troubleshooting network connectivity (e.g., using ping to check if a host is reachable).
3. IGMP (Internet Group Management Protocol)
- Description: IGMP manages multicast group membership, allowing devices to join or leave multicast groups.
- Functions:
- Enables efficient transmission of data to multiple recipients (multicasting).
- Use Case: Streaming video to multiple users simultaneously, such as live video broadcasting.
4. RIP (Routing Information Protocol)
- Description: RIP is a distance-vector routing protocol that uses hop count as a routing metric to determine the best path for data.
- Functions:
- Shares routing information with other routers in the network.
- Limits the number of hops allowed to avoid routing loops (maximum of 15 hops).
- Use Case: Small and simple networks, where routing is straightforward and limited in size.
5. OSPF (Open Shortest Path First)
- Description: OSPF is a link-state routing protocol that uses the Dijkstra algorithm to find the shortest path for data transmission.
- Functions:
- Routes packets dynamically based on network changes and link states.
- Converges quickly and provides scalable routing in larger networks.
- Use Case: Large enterprise networks and ISPs that require efficient and fast routing.
6. BGP (Border Gateway Protocol)
- Description: BGP is a path-vector protocol that determines the best routes between autonomous systems (AS) on the internet.
- Functions:
- Manages the routing of data between different networks (AS) on the internet.
- Makes routing decisions based on various policies and metrics, such as network reachability.
- Use Case: The backbone of internet routing, used by ISPs to route traffic between different networks.
7. NAT (Network Address Translation)
- Description: NAT allows a single public IP address to be shared by multiple devices within a private network.
- Functions:
- Translates private IP addresses to a public IP address when communicating over the internet.
- Conserves the limited supply of public IP addresses.
- Use Case: Home or office networks, where multiple devices share the same internet connection.
8. ARP (Address Resolution Protocol)
- Description: ARP is used to map IP addresses to MAC addresses within the same network.
- Functions:
- Converts a device’s logical IP address into its physical MAC address for data transmission on local networks.
- Use Case: Used in LAN environments to locate devices when sending data.
9. VPN (Virtual Private Network) Tunneling Protocols
- Description: VPN protocols such as IPsec (Internet Protocol Security) and GRE (Generic Routing Encapsulation) operate at the Network Layer to provide secure communication over the internet.
- Functions:
- Encrypts and tunnels network traffic between devices.
- Use Case: Secure communication between remote users and private networks (e.g., remote workers accessing a corporate network).
10. IS-IS (Intermediate System to Intermediate System)
- Description: IS-IS is a link-state routing protocol similar to OSPF, designed to move data efficiently within a large network.
- Functions:
- Finds the best path for data within a network using the shortest path first (SPF) algorithm.
- Use Case: Often used in large-scale service provider networks.
Functions of the Network Layer:
- Logical addressing: Assigns and manages IP addresses for devices.
- Routing: Determines the best path for data to travel from source to destination across multiple networks.
- Fragmentation: Breaks down large packets into smaller ones to fit the maximum transmission unit (MTU) of the network.
- Packet forwarding: Moves packets between networks, using routers to direct data to the correct destination.
- Error handling and diagnostics: ICMP provides feedback on issues like unreachable destinations or congestion.
The Network Layer is essential for delivering data between networks, enabling the internet and wide-area communications. Protocols like IP, BGP, OSPF, and ICMP play crucial roles in ensuring data is routed efficiently and accurately.
The Data Link layer is the second layer of the OSI model and is responsible for node-to-node communication, error detection and correction, and the management of physical addressing. It ensures that data is transferred between adjacent network nodes within the same local area network (LAN).
Common Examples of Data Link Layer Components and Protocols:
- Ethernet (IEEE 802.3)
- Description: The most common wired LAN technology.
- Function: Defines how devices on a network access the medium (cabling) and format data frames for transmission over the network.
- Example: Ethernet cables (e.g., Cat5, Cat6) and switches used in home or office networks.
- Wi-Fi (IEEE 802.11)
- Description: The standard for wireless LANs (WLANs).
- Function: Handles wireless communication between devices and a wireless router or access point.
- Example: The wireless connection between your laptop and a Wi-Fi router.
- PPP (Point-to-Point Protocol)
- Description: A protocol used for direct communication between two nodes.
- Function: Encapsulates data for transmission over serial links, such as those used in dial-up connections or DSL.
- Example: Internet service providers (ISP) using PPP to establish a connection between a user’s modem and the internet.
- Frame Relay
- Description: A data link layer protocol designed for telecommunication networks.
- Function: Provides a fast and efficient method for transmitting frames across a network over a shared medium.
- Example: Often used in wide area networks (WANs) to connect multiple locations.
- ATM (Asynchronous Transfer Mode)
- Description: A protocol that operates at the Data Link layer and is used for high-speed networking.
- Function: Transmits data in fixed-size cells, making it suitable for real-time voice and video transmission.
- Example: Used in telecommunications to handle voice, video, and data traffic on the same network.
- HDLC (High-Level Data Link Control)
- Description: A bit-oriented protocol used in point-to-point and multipoint connections.
- Function: Manages error correction, flow control, and data framing.
- Example: Utilized in leased-line WAN connections between routers.
- MAC (Media Access Control)
- Description: Part of the Data Link layer that handles addressing and channel access.
- Function: Assigns unique MAC addresses to devices on the same network and controls how devices access the shared medium.
- Example: Your network card’s MAC address in an Ethernet or Wi-Fi network.
- ARP (Address Resolution Protocol)
- Description: A protocol for mapping an IP address to a physical machine (MAC) address in a local network.
- Function: Translates logical addresses (IP) to physical addresses (MAC).
- Example: A device using ARP to find the MAC address of a device in a local network.
The Physical Layer (Layer 1) and the Data Link Layer (Layer 2) work closely together in the OSI model, but they have distinct roles. The Physical Layer is responsible for the transmission and reception of raw bits over a physical medium (like wires, radio waves, etc.), while the Data Link Layer is responsible for organizing bits into frames and ensuring reliable data transfer between two directly connected devices.
Examples of Physical Layer (Layer 1)
- Ethernet Cables (Twisted Pair, Coaxial, and Fiber Optic Cables)
- Description: Physical cables that carry electrical signals or light pulses between devices.
- Function: Transmit data as electrical signals (twisted pair/coaxial) or light pulses (fiber optic).
- Use Case: Wired connections between computers, switches, routers, etc.
- Wi-Fi (Wireless Fidelity) – IEEE 802.11
- Description: Wireless communication technology that uses radio waves to transmit data.
- Function: Transmits bits wirelessly between devices like laptops and routers.
- Use Case: Provides wireless internet access in homes, offices, and public areas.
- Bluetooth
- Description: A short-range wireless communication standard.
- Function: Transmits data over short distances (up to 100 meters) using radio waves.
- Use Case: Used for connecting peripherals like keyboards, mice, or headphones to computers and smartphones.
- Hubs
- Description: Networking devices that connect multiple Ethernet devices in a LAN.
- Function: Broadcasts electrical signals (data) to all connected devices in the network.
- Use Case: Simplistic LAN setups, although largely replaced by switches.
- Optical Transceivers
- Description: Devices that convert electrical signals into optical signals for fiber optic communication.
- Function: Encodes and decodes light pulses for data transmission via fiber optic cables.
- Use Case: Used in high-speed networking environments, such as in data centers or long-distance communications.
- DSL (Digital Subscriber Line)
- Description: A technology for transmitting digital data over telephone lines.
- Function: Carries digital signals over copper telephone lines to provide internet service.
- Use Case: Home broadband internet access.
- Modems (Modulator-Demodulator)
- Description: Devices that convert digital data into analog signals and vice versa.
- Function: Modulates digital data into analog signals for transmission over phone lines and demodulates incoming analog signals into digital data.
- Use Case: Used in dial-up internet or DSL connections.
- Radio Frequencies (RF)
- Description: Uses electromagnetic waves to transmit data wirelessly.
- Function: Converts bits into radio frequency signals for wireless transmission.
- Use Case: Used in Wi-Fi, mobile phones, satellite communication, and NFC (Near Field Communication).
- NIC (Network Interface Card)
- Description: Hardware component in a computer that connects it to a network.
- Function: Transmits and receives data between a computer and the physical network.
- Use Case: Provides Ethernet or wireless connections for desktop or laptop computers.
- RS-232
- Description: A standard for serial communication transmission of data.
- Function: Used for simple, low-speed data communication over cables.
- Use Case: Connecting modems, printers, or other peripherals to computers.
Here we have list down in great detail the types of services we have categorized under each layer for easier to understand the world of compute and networks but better debug or troubleshooting experience we will refer the TCP/IP model in future blog post.

Leave a Reply